Microsoft has recently announced that custom compliance hit general availability, which is really good because it is a very useful feature, that allows to extend monitoring of devices past standard compliance policy options, without the need of any 3rd party services.
However, in a secure environments there is one big issue with this. The default discovery script interval is 8 hours, meaning, scripts are rerun very rarely. Someone could change a setting, and not be blocked within a reasonable timeframe.
Today I was playing with custom compliance, as I plan to introduce it for some security settings that I want to be monitored, and the access to certain resources within the company limited if found to be disabled.
So I began by creating a discovery script. Then, created a corresponding JSON file, and waited for results, which ended up being satisfying – both settings were configured, and were in fact showing as compliant in Intune, hurray! 🍾
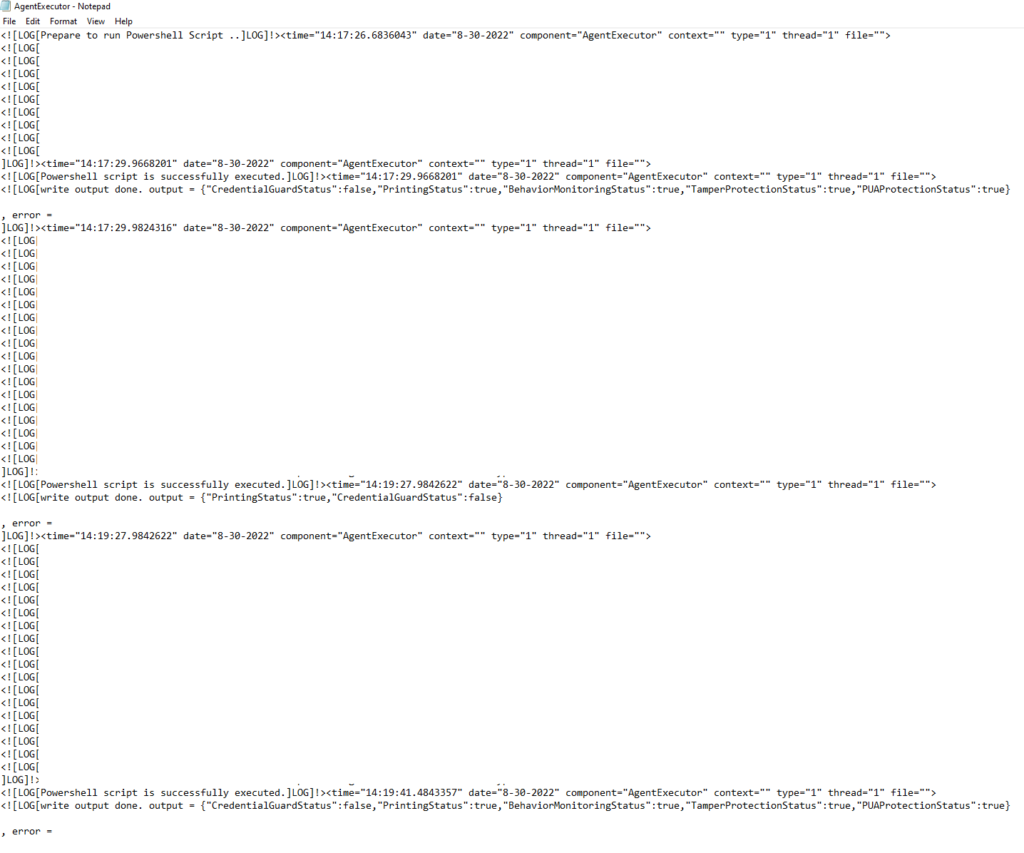
Then I started changing those settings and have noticed that manual sync doesn’t actually rerun the script, therefore even after alteration to these settings on the machine, they were still both compliant and they would be, until next script run cycle. Each manual sync didn’t increment the last modified timestamp of AgentExecutor.log which shows PowerShell/Remediation scripts logs.
This got me thinking whether expediting this would be possible, started looking for some information and stumbled upon Oliver’s blog post: Triggering Intune Management Extension (IME) Sync – Modern IT – Cloud – Workplace (oliverkieselbach.com)
I have used strings to find out if there is anything other than intunemanagementextension://syncapp and found that intunemanagementextension://synccompliance also exists!
The last missing piece was using Run (Win+R) and running this command.
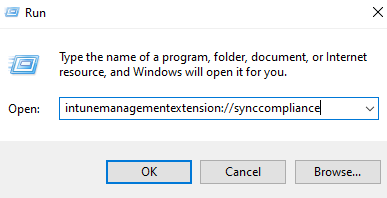
This, to my surprise, resulted into the AgentExecutor.log update (immediately!) , and after roughly two minutes – the report in Intune has also changed, settings that had been compliant, were not compliant anymore!
As you can see in the screenshot below, you can rerun the detection script pretty often 🙂
I guess the very last part, which I’ll probably save for the next post, will be adding this command to a PowerShell script, and then inside a Task Scheduler job, which will automate it 🙂
 Marcin Szafrankiewicz
Marcin Szafrankiewicz